Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
view the rest of the comments
But if I correctly understand how Tailscale works I would need to install tailscale on all machines I wish to give access to friends?
No, installing Tailscale on all machines is not actually required. You can setup a funnel that exposes a service to the internet for all to see. This also removes the requirement for them to access via Wireguard if desired. https://tailscale.com/kb/1223/funnel
Yes.
Otherwise, just open up ports on your network firewall and set up DNS to point to your external ip.
There might be a way to do this with cloudfare that is more secure.
Edit: you might want to create a network diagram to help explain what you have and what you want to do. The way you describe the problem is confusing.
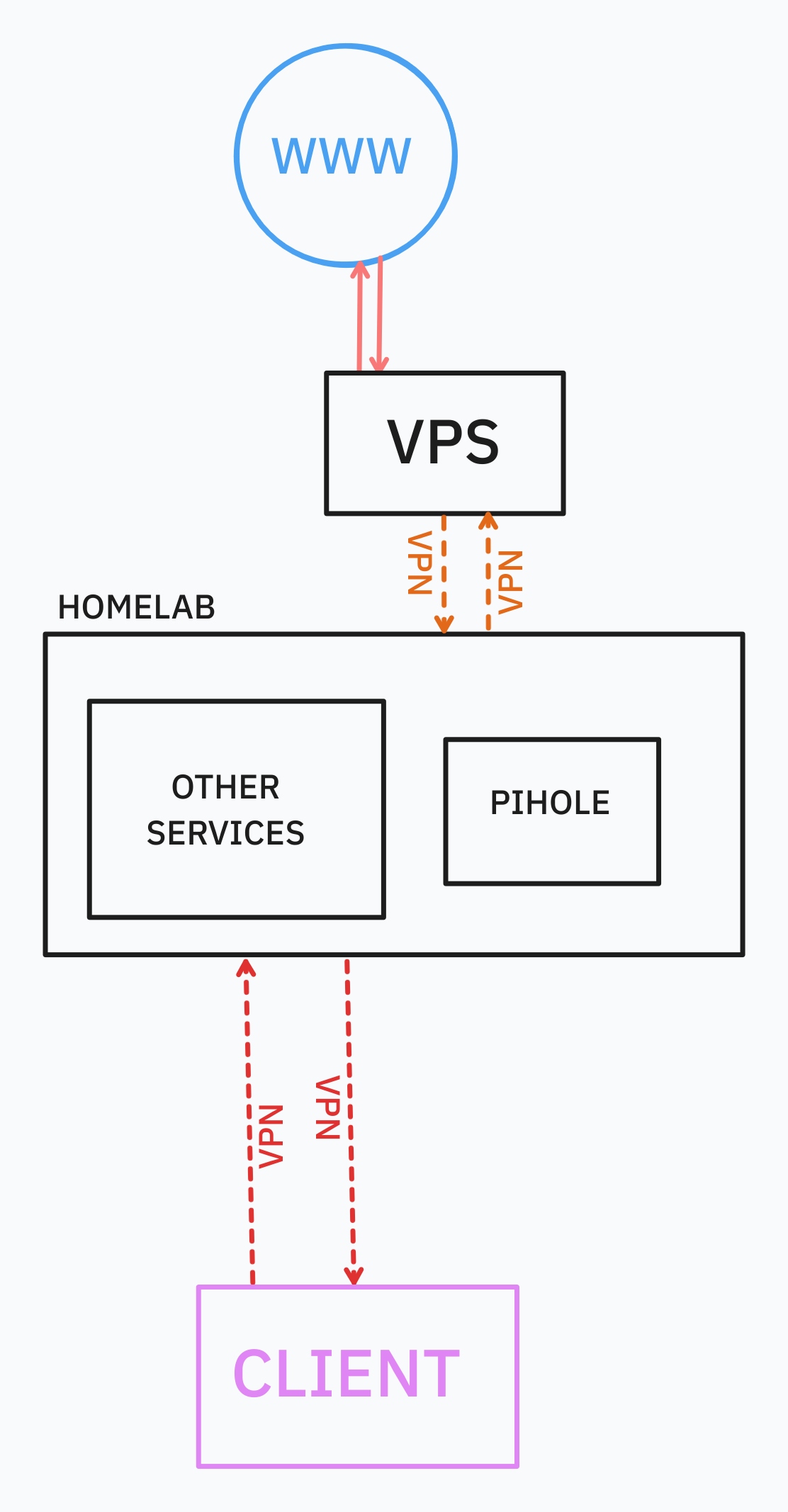
Edited the post with a diagramm
From the diagram you just want to put everything within a vpn so they are on the same network.
You can choose whatever vpn solution you want but I like Tailscale since you don’t need to set up any inbound nat or firewall.
From the diagram it looks like you want your outside clients to use vpn as well.
Nah it's not what I want to do.
The request from client for local services goes trough the first VPN and are resolved in my home and then comeback.
The request from client to outside services goes trought my home with the first VPN, are resolved here and then go to the internet trough the second VPN and then comeback to the client
What you’re describing is overly complex routing, and split DNS.
Join all clients to a single network.
I want to protect my home services, so when accessing my domain it goes trough the vps and you only knows its IP (a datacenter IP) but for my friends and family I don't need this protection so they are accessing my home with a VPN connection and btw they are using the vps to make requests and so protect their privacy.
The simple solution (since my services are publicly available), would be to route all traffic coming from my friends trough my home and then through the vps. But I don't like this idea since it would add a lot of latency and useless traffic since the client is already going trough my home...
So my question is how could I route directly to the client the local services and let go through the vps the rest of the traffic?
The answer here is still a single vpn, and Tailscale makes this even easier.
Don't think so, but I will try to check it
Right will try to make you a diagram, but I dont think tailscale would be a good solution...
Cloudflare tunnels does exactly this....